News
Own this garage door opener? Shut it down; hackers can target it
The main takeaway is for owners to unplug these devices until all of this is sorted out if that ever happens.
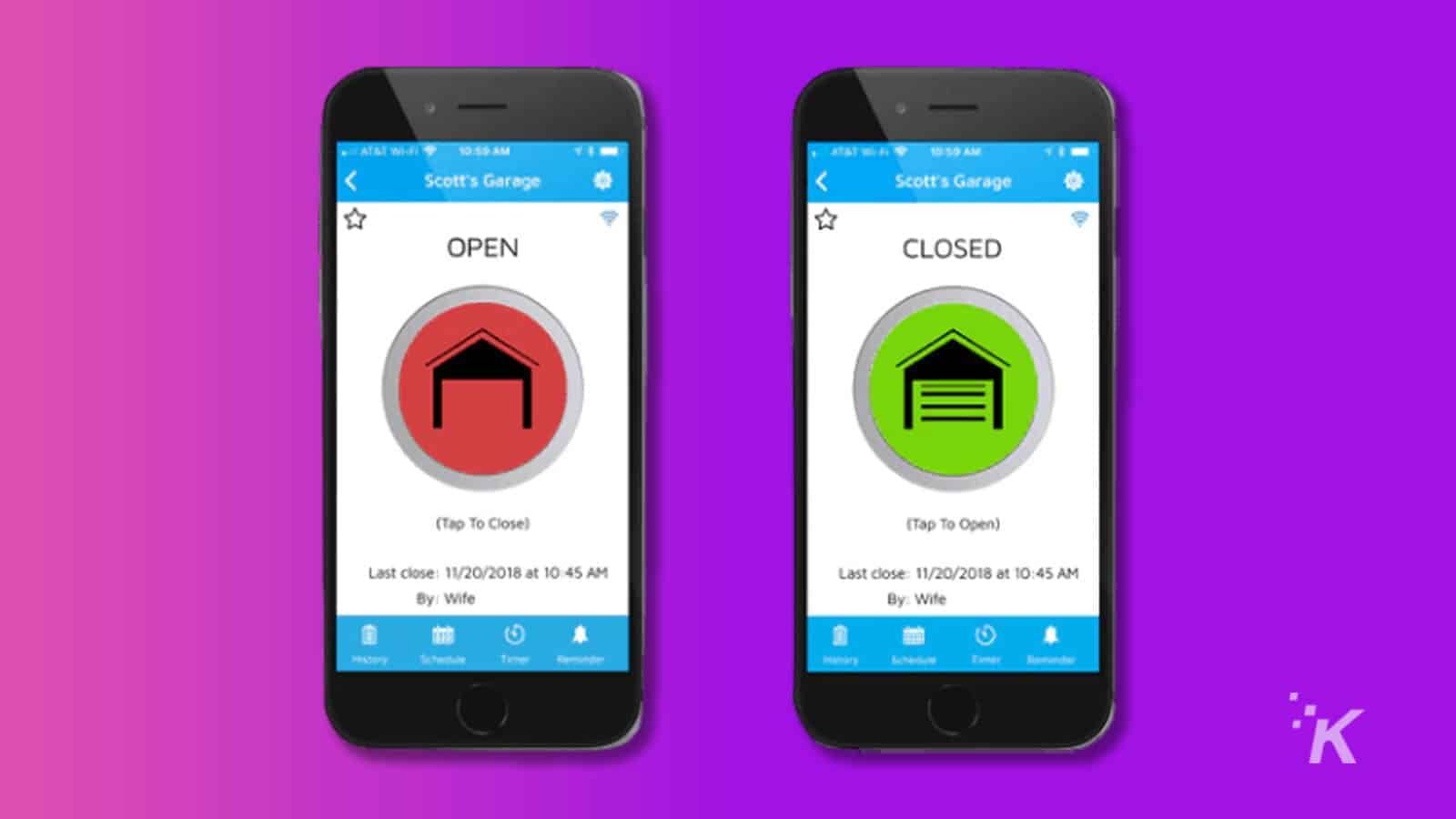
If you’re using a popular garage door controller made by Nexx, we’ve got some bad news.
These devices are extremely vulnerable to hackers and it’s time to consider unplugging the device until this mess gets sorted out.
Apparently, any hacker or hobbyist with a little technical know-how can prance down the street and simply open your garage door at the push of a button.
Now, you might wonder if a sophisticated hacker or bot network is behind this.
Surprisingly, no – the researcher who made the discovery found that a simple $80 remote control was all it took to exploit the vulnerability.
Here’s what it looks like
Things get a tad technical from this point, but the core issue revolves around Nexx devices designed to operate garage doors.
It turns out, the gadget relies on an easily discoverable password and exposes personal information such as names and email addresses.
It even inadvertently instructs others on how to open doors or operate plugs.
Sam Sabetan, the researcher who initially uncovered the problem, took to Medium to express his concerns and highlight the lack of action being taken to address the issue.
“Nexx has consistently ignored communication attempts from myself, the Department of Homeland Security, and the media,” wrote Sabeten in a post published on Medium. “Device owners should immediately unplug all Nexx devices and create support tickets with the company requesting them to remediate the issue.”
How many customers are affected?
As it stands, the researcher says there’s about 40,000 of these garage door openers out there and urges customers to unplug them until the company figures this out.
But as we can see, they’re not even taking ownership of it.
Thankfully, per Ars Technica, the US Cybersecurity and Infrastructure Security Agency issued an advisory that suggests users take defensive measures, including:
- Minimizing network exposure for all control system devices and/or systems, and ensure they are not accessible from the Internet.
- Locating control system networks and remote devices behind firewalls and isolating them from business networks.
- When remote access is required, use secure methods, such as virtual private networks (VPNs), recognizing VPNs may have vulnerabilities and should be updated to the most current version available. Also recognize VPN is only as secure as its connected devices.
For those eager to delve deeper into the technical details, we recommend reading Sabetan’s Medium article and this informative Ars Technica piece to truly grasp the ins and outs of the situation.
For me, the main takeaway is for owners to unplug these devices until all of this is sorted out, if that ever happens.
We reached out to Nexx but they did not immediately respond to our request for comment. We’ll update the post if we hear anything back.
Editors’ Recommendations:
- A major new Android bug lets hackers take over your devices
- Google Home speakers were at risk of eavesdropping hackers
- ‘Bahamut’ hackers target Android users with phony VPN apps
- A hacker leaked tons of GTA 6 early gameplay footage (updated)
Just a heads up, if you buy something through our links, we may get a small share of the sale. It’s one of the ways we keep the lights on here. Click here for more.